Intune has got your back when it comes to securing your mobile apps on iOS and Android devices. With its App protection policies feature, Intune Mobile Application Management (MAM) ensures that your corporate data is safe and sound. This protection is applicable for all supported apps (from partners and Microsoft) on mobile devices that are either managed (Intune MDM Enrolled) or unmanaged (Without Enrollment). The Intune MAM takes care of the latter and makes sure your Bring Your Own Devices (BYOD) stay secure without the need for full device management (Intune MDM or third-party).
The Intune MAM is like a superhero that specializes in app-level protection, allowing sandboxing and controlling where your corporate data can be pasted. And if that wasn’t enough, with the Intune MAM combined with Azure AD Conditional Access, you get the extra perk of enforcing checks for the App protection policy on a mobile device for supported apps. So if the protection policy is not available, access to the cloud app will be denied right after the user authenticates.
What do we need ?
If you’re diving into the world of Intune, there are a few things you need to know about supported operating systems. For starters, make sure you’re running at least the minimum OS version required.
If you’re using an unmanaged device, aka BYOD, you’ll need Microsoft Authenticator on your iOS and Microsoft Company Portal on your Android. Don’t worry, they’re your new best friends.
Next up, you’ll want to check out Intune Data Protection Framework, which offers App Protection Policies. Want to know more about importing JSON templates with recommended settings? Check out my other blog for all the juicy details.
Don’t forget about Intune MAM protected apps. There’s a whole list of supported apps with the Microsoft Intune App SDK embedded, so you can rest easy knowing your apps are secure.
And last but not least, Conditional Access (CA) policy. This requires an Azure AD Premium P1 license (part of EMS E3 / E5 bundle). To give you an idea, you can set an example policy that requires approved client apps or app protection policy. Now that’s what we call keeping it conditional.
Let’s dive into the exciting world of configuring App protection policies! Don’t worry, we’ll make it easy for you.
First things first, we recommend importing JSON templates files with best-practice policy settings. You can choose between three levels of data protection: Basic, Enhanced, and High. For unmanaged devices in a business environment, we suggest going with Level 2 (Enhanced) with some customized settings and rename it.
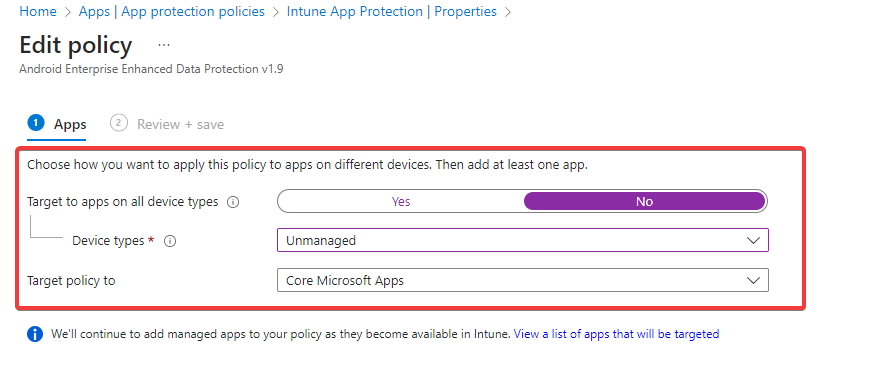
Now, when assigning your App protection policy, you have a couple of options. You can target all device types or just unmanaged ones. For the latter, you can assign the policy to all apps or only the core Microsoft ones. In our case, we assign the policy to the BYOD MAM group of privileged users.
For Managed device types, you can configure a second policy with fewer restrictions since there should be other MDM security policies and profiles in place.
Next up, let’s talk about Conditional Access.
This feature allows you to require a check for an App protection policy to be present on the client app before access is provided to selected cloud apps. To register a mobile device in Azure AD, you’ll need a broker app. For iOS, we recommend the Microsoft Authenticator, and for Android, the Microsoft Company Portal.
When creating a Conditional Access policy, you can set the cloud app condition to all apps and the device platforms to iOS and Android. You can also choose to require either an app protection policy or an approved client app.
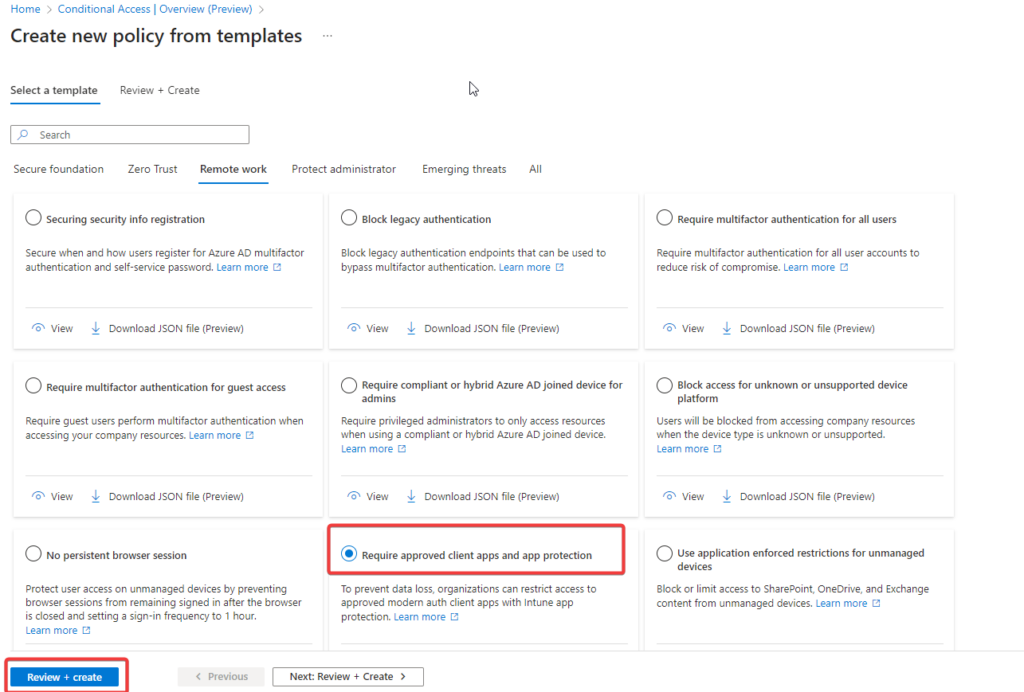
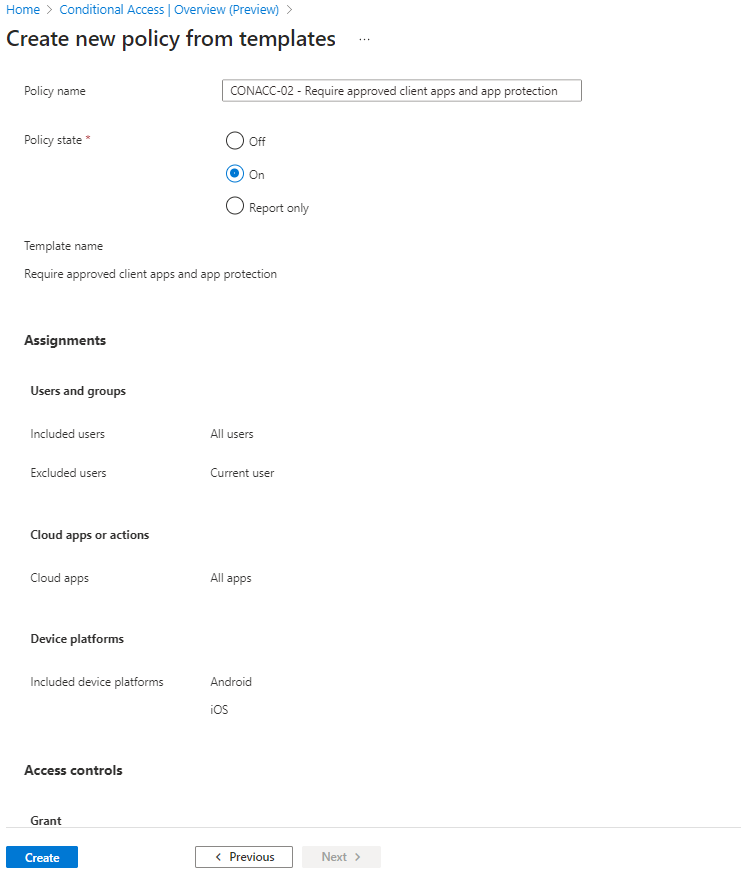
The user experience is straightforward. Once they download the Microsoft Outlook app on their unmanaged iPhone and sign in with corporate credentials, they’ll be redirected to the App Store to download the Microsoft Authenticator (if they don’t already have it). The broker app will start the Azure AD registration process, creating a device record in Azure AD.
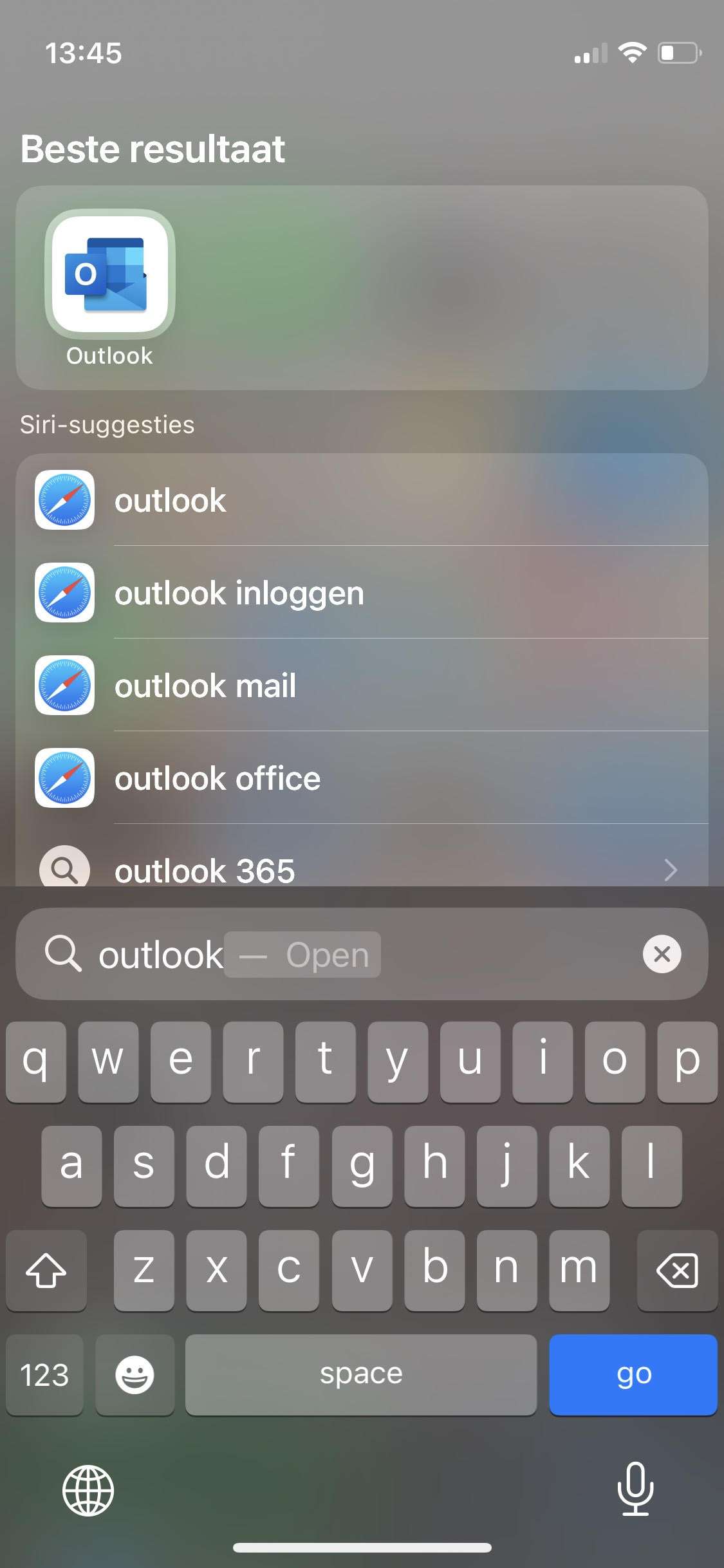
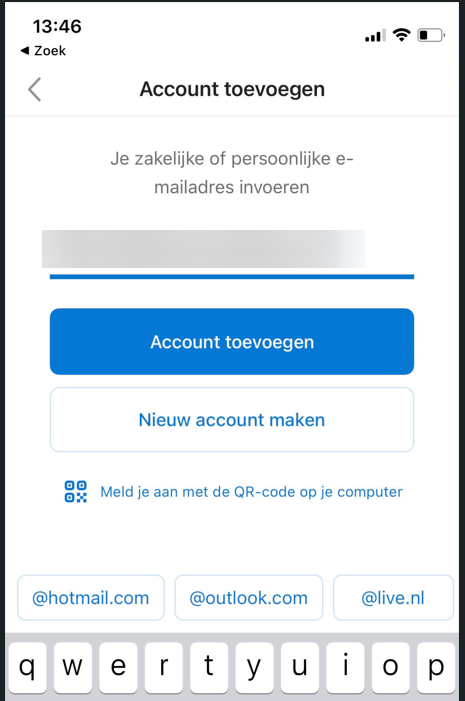
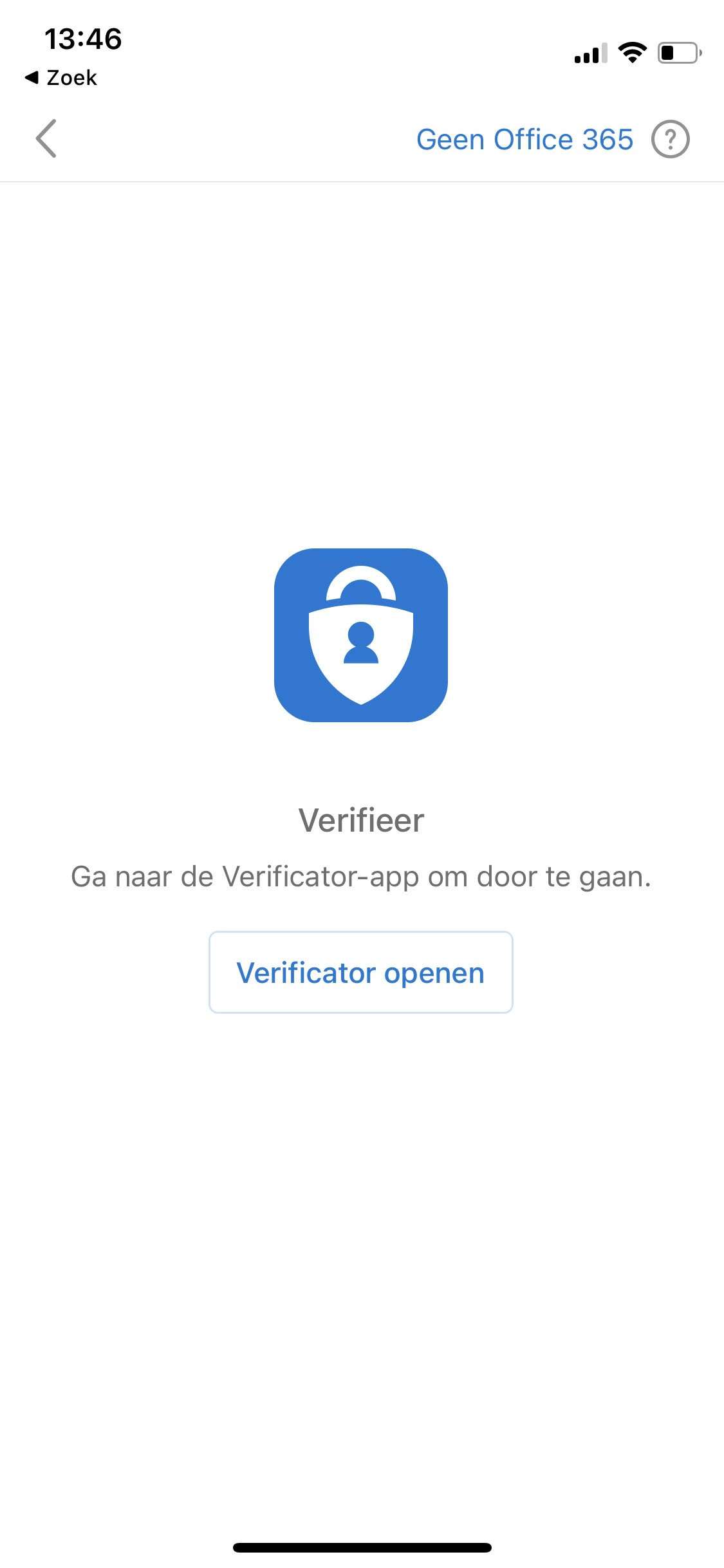
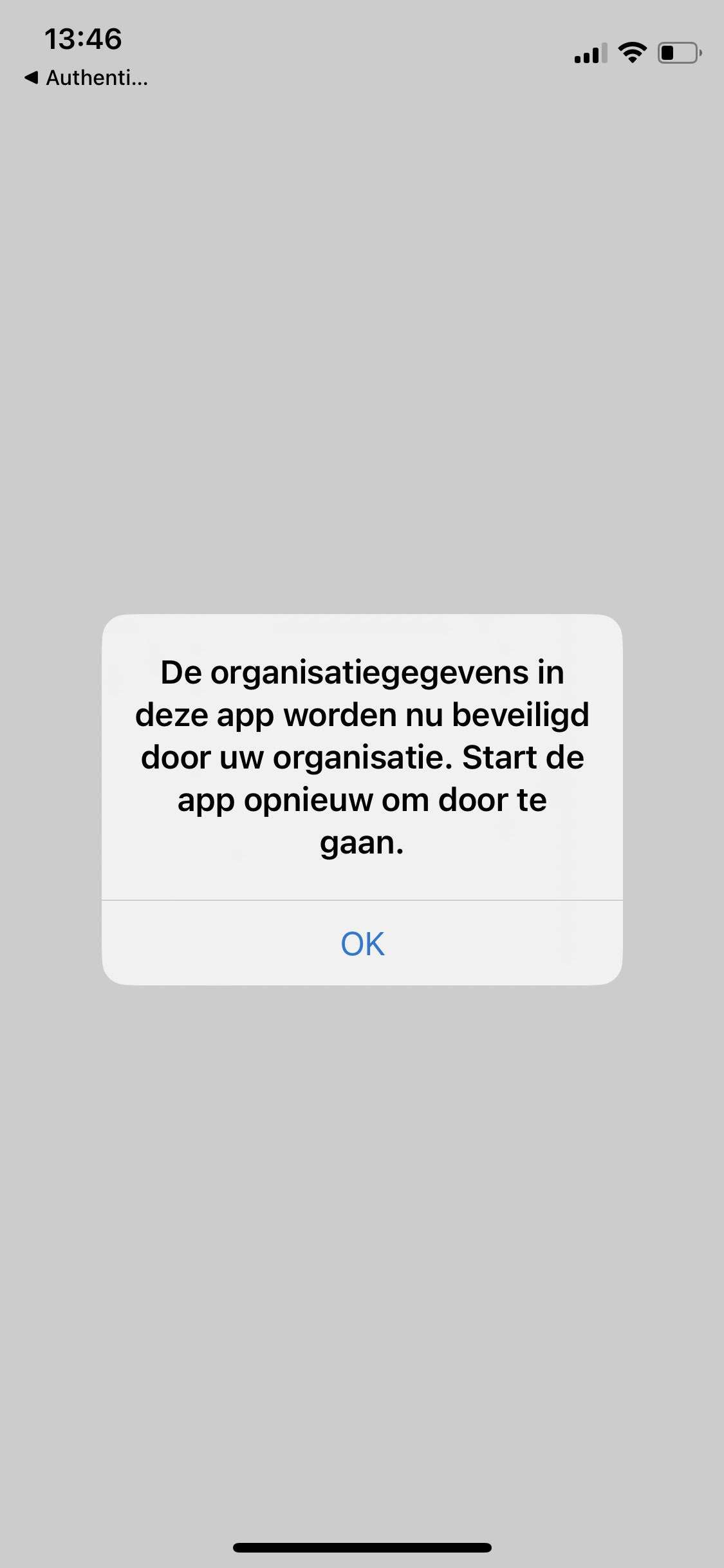
Finally, make sure your App protection policies are applied; otherwise, access will be blocked. And remember, the user needs to set up a PIN for app access, which is shared between other apps from the same publisher (Outlook, Teams, Edge, etc.). With all these security measures in place, your corporate data is safe and sound!
