If only there were a framework we could use… Oh, wait, there is! Introducing the Data Protection Framework, a suit of armor for your apps and data on mobile devices (iOS/Android). These preconfigured and recommended App Protection Policies (APP) are like the wardrobe of a medieval knight, just a tad bit more high-tech and definitely less rusty! They’re somewhat akin to the Security Configuration Framework used for toughening up Windows 10/11 devices.
The APP Data Protection Framework comes in three fashionable configurations:
Level 1 enterprise basic data protection (the bow tie)
Level 2 enterprise enhanced data protection (the comfy sneakers)
Level 3 enterprise high data protection (the ultimate superhero cape)
To spot the differences in style and substance between Levels 1, 2, and 3, I recommend taking a peek at the links above. Make sure to go through the policy settings in detail before importing and applying them to supported apps (Intune protected apps) on your mobile devices.
In this blog post, I’ll play the role of your friendly Neighbour and show you how to import the policy sets (JSON templates) that contain the App Protection Policies (Data Protection Framework) to MEM/Intune.
Setting the Stage: Prerequisites
- Ensure you have a Microsoft Endpoint Manager (Intune) tenant with MDM authority set to Intune.
- Acquire the APP Data Protection Framework:
- Download the Intune-Config-Frameworks-master.zip file from GitHub.
- Obtain the PowerShell script ManagedAppPolicy_Import_FromJSON.ps1 needed for importing the JSON templates (App Protection Policies).
- Note: First-timers will need Global Administrator permission to use these scripts.
Remember: You can find the rest of the prerequisites for importing JSON files in the README.md file within the .ZIP bundle.
Let’s Dive into Configuration!
- App Protection Policies (APP):
On a Windows 10/11 machine equipped with the AzureAD PowerShell module,
- Unzip the Intune-Config-Frameworks-master.zip file and locate the AppProtectionPolicies folder.
- Download the ManagedAppPolicy_Import_FromJSON.ps1 PowerShell script and place it in the AppProtectionPolicies folder.
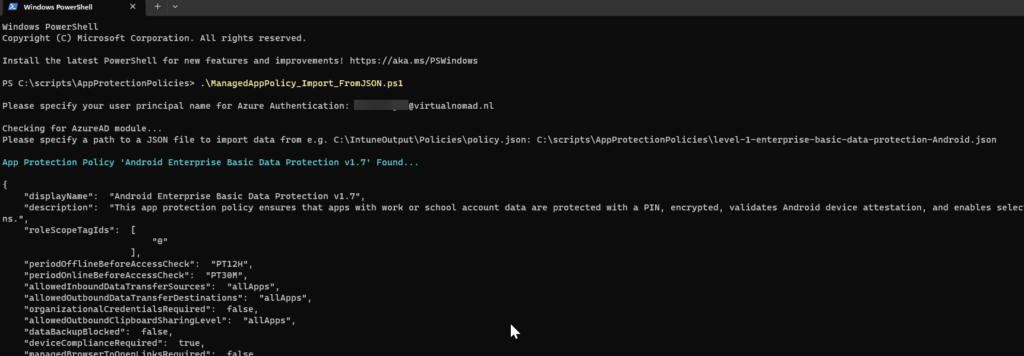
- Open an elevated PowerShell prompt, navigate to the AppProtectionPolicies folder, and run the import PS script: .\ManagedAppPolicy_Import_FromJSON.ps1
PS C:\scripts\AppProtectionPolicies> .\ManagedAppPolicy_Import_FromJSON.ps1- When prompted for your user principal name for Azure Authentication, input your Global Administrator account and password for the first run of the script. After that, you won’t see this prompt for around 60 minutes.
Note: In subsequent script runs, when prompted for authentication with an Azure AD account, you can use an Intune Administrator account with a valid license.
- Next, you’ll be prompted to specify a path to a JSON file for importing data. Since all the files are in the same folder as the PowerShell script, simply providing the file name should suffice. Repeat the process until you import all JSON templates (App protection Policies):
- level-1-enterprise-basic-data-protection-Android.json
- level-1-enterprise-basic-data-protection-iOS.json
- level-2-enterprise-enhanced-data-protection-Android.json
- level-2-enterprise-enhanced-data-protection-iOS.json
- level-3-enterprise-high-data-protection-Android.json
- level-3-enterprise-high-data-protection-iOS.json
Log in to Microsoft Endpoint Manager (endpoint.microsoft.com) and go to Apps -> App protection policies to ensure successful policy imports.
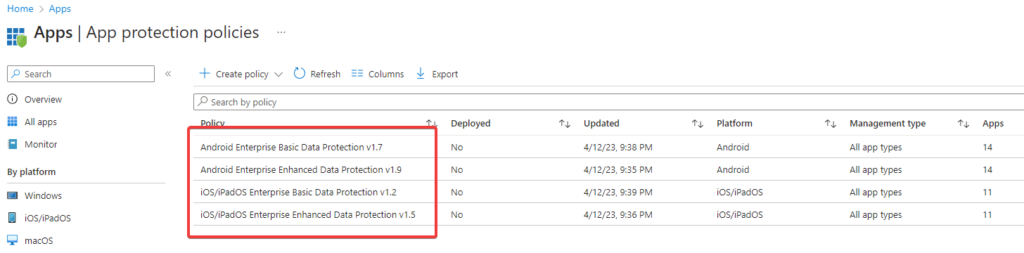
Review the APP policies in the MEM/Intune console (if not done previously in JSON files), make necessary changes to match your security requirements, add or remove applications from the default app list, and set the required management type for the policies to apply:
- iOS/iPadOS can be set as Managed or Unmanaged (BYOD)
- Android can be set as Unmanaged (BYOD), Android Device Admin, or Android Enterprise.
OPTIONAL: Device Configuration profiles and Compliance policies
In the same ZIP bundle (Intune-Config-Frameworks-master.zip), you’ll find an AndroidEnterprise folder containing two subfolders: FullyManaged and WorkProfile.
Inside, you’ll discover Device Configuration profiles and Compliance policies that you can import using two more PowerShell scripts and following similar steps as before:
These Device Configuration and Compliance policy templates can be used to strengthen your Android Enterprise devices (Work Profile and Fully Managed), on top of the security already applied to mobile apps through App Protection Policies.
Stay Tuned for More!
We hope you found this guide helpful for importing and configuring App Protection Policies. But wait, there’s more! I’m currently working on another blog post that will dive deeper into configuring various aspects of your policies and devices to further enhance your organization’s data security.
So, keep an eye out for our upcoming blog – we’ll be back soon with even more insights, tips, and tricks to help you make the most of your MEM/Intune experience. Happy configuring!

