Many businesses allow guest access to their digital systems but don’t pay much attention to how it’s managed. They skip planning to keep things moving smoothly. Despite this, guest access is common in many places. By looking closer at how guest accounts are handled, companies can keep things running well while making sure their systems are secure
Why should you consider having guest users in our domain? The answer often boils down to collaboration and temporary engagements. Here are the typical scenarios:
- Project Collaboration: When you’re teaming up with external partners on a project, granting them access to relevant Microsoft Teams channels ensures seamless communication and collaboration.
- Sharing Resources: If there’s a need to share documents or other resources housed on a SharePoint site, guest access becomes essential.
- Temporary Support: Hiring someone on a temporary basis for support? A guest account is your go-to solution to provide them the necessary access without compromising on security.
In each of these scenarios, managing guest access efficiently is crucial to maintain a secure and productive working environment.
The Microsoft Entra admin center has some settings for guest users. Below are the common ones.
- Guest invite settings
- Restrict the Access Permissions of Guest Users
- Ensure Safe Guest Access with Conditional Access
- Limit invitations
Guest Invite Settings
One setting in Azure AD lets you decide who can invite guests to your network. It’s essential for every organization to find what suits them.
External Identities | External collaboration settings:
A common choice for many organizations is to allow both member users and certain admin roles to invite guests, ensuring that work stays on track. This setting means that specific admins, like those with the guest-inviter role, along with team members, can send out guest invites.
For tighter control over guest access, organizations can opt to permit only certain users, based on their group membership, to have the guest-inviter admin role. They can then set it so only these specific admins can invite guests. This approach offers a structured way of managing guest invitations while maintaining a secure and orderly system.
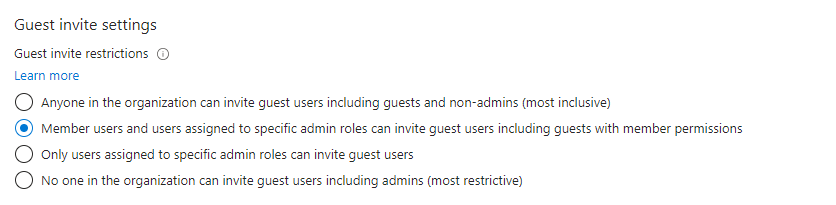
To limit who can invite guests in Azure AD using Microsoft Graph PowerShell, do the following
Get the latest Microsoft Graph PowerShell module and connect to Microsoft Graph:
Connect-MgGraph -Scopes Policy.ReadWrite.AuthorizationAfter that change the settings with the command below:
Update-MgBetaPolicyAuthorizationPolicy -authorizationPolicyId authorizationPolicy -AllowInvitesFrom adminsAndGuestInvitersYou can set Set -AllowInvitesFrom to: none, adminsAndGuestInviters, adminsGuestInvitersAndAllMembers, or everyone to control who can invite guests.
Restrict the Access Permissions of Guest Users
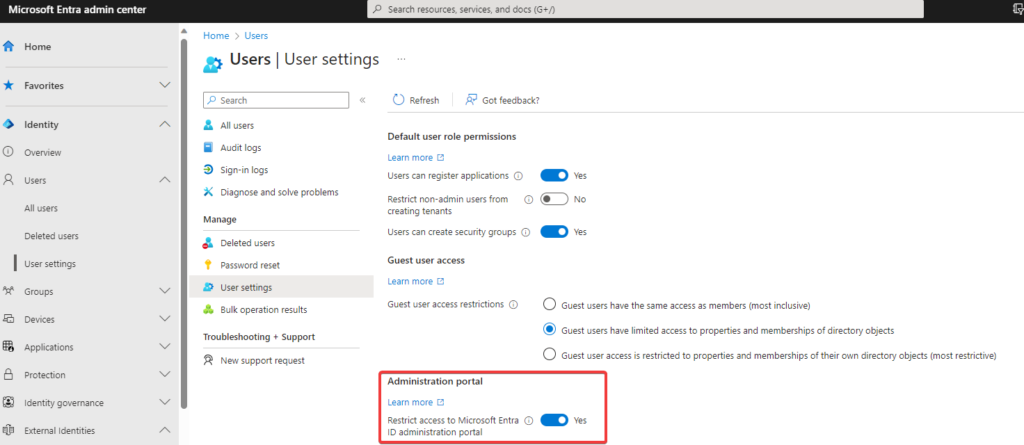
When inviting a guest, it’s important to restrict their rights to keep certain data hidden. For instance, you might want to limit their access to the Entra ID administration portal where they could view tenant information. To do this, go to Entra Admin Center > Identity > Users > User Settings > Administration portal > Restrict access to Microsoft Entra ID administration portal.
Ensure Safe Guest Access with Conditional Access
Giving a guest user access is quick and easy. But how can you make sure they log in securely? The solution is Conditional Access. To have each guest go through two-factor authentication at login, you need to set up a Conditional Access rule for guests. Remember, you’ll need at least one Azure AD Premium (AAD) P1 license on your tenant to use Conditional Access. One AAD P1 license covers P1 features for up to five guests. Below is an image showing the Conditional Access policy set up for guests:
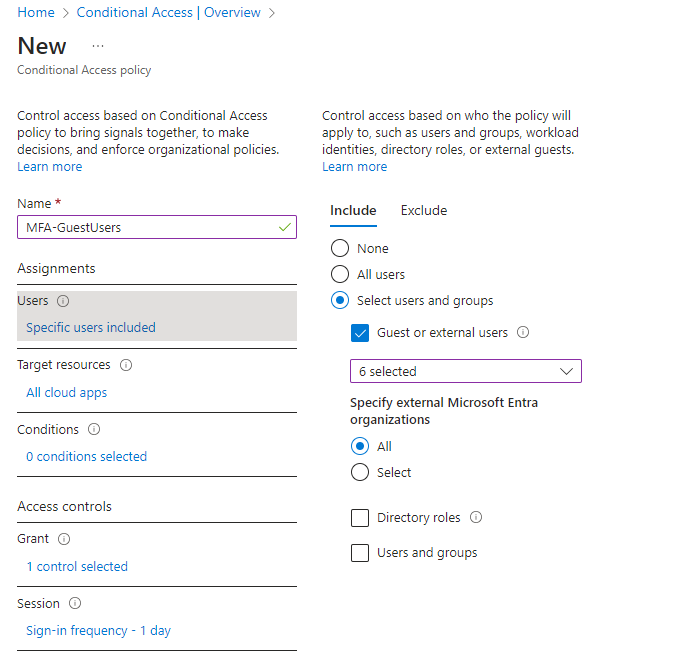
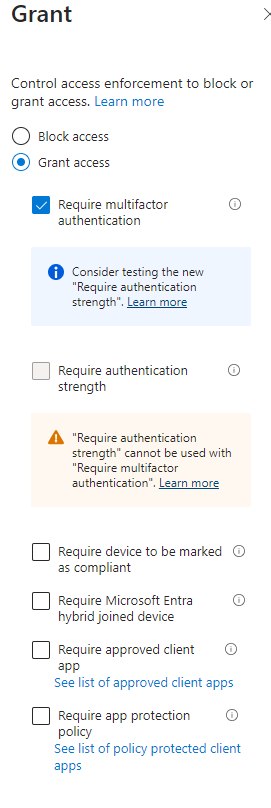
Limit invitations
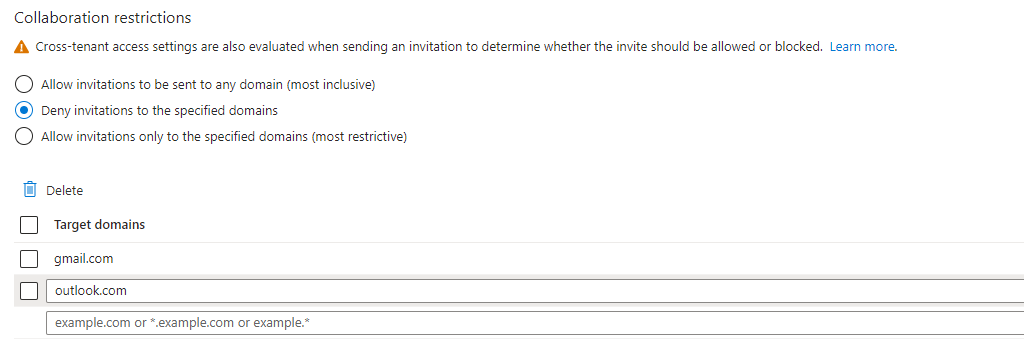
Besides giving guest access, a company should decide which domains can enter its environment. For example, should access from personal domains like @gmail.com or @outlook.com be allowed? You can block certain domains in the Entra Admin Center by going to Identity > External Identities > External Collaboration Settings > Collaboration Restrictions > Deny Invitations to Specified Domains.
Summary
Many businesses allow guest access to their systems for collaboration, sharing resources, or temporary support, but often overlook proper management of this access. It’s important to handle guest accounts efficiently to ensure security and smooth operations. Microsoft Entra offers various settings to control guest access, like who can invite guests and what domains can be allowed. I hope this blog has helped you better understand and manage guest access securely.

