Today, we’re diving into the fascinating world of multi-factor authentication (MFA) and its not-so-equal siblings. Just like in a dysfunctional family, not all MFA methods are created equal. Some are like the overprotective parent who won’t let you do anything without a permission slip, while others are as reliable as your forgetful uncle who constantly misplaces his keys. We’ll navigate through the pitfalls of certain MFA approaches and explore the importance of choosing robust authentication methods to keep those cyber villains at bay.
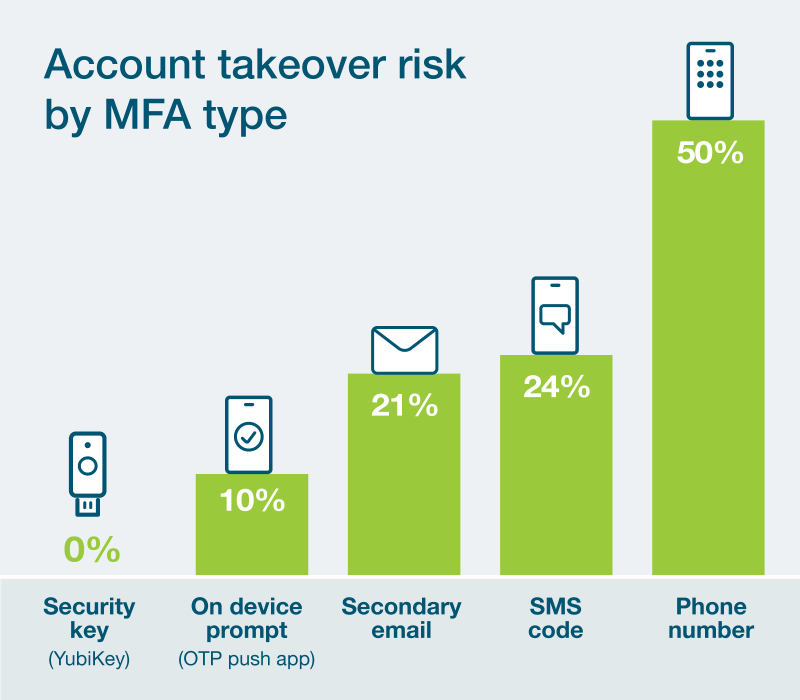
There are various types of MFA used in organizations. It is now clear that voice and SMS authentication are out of the question. However, many companies still have users who have these methods set up, making a transition to other options not so straightforward. This transition will take time. To address this, Microsoft has introduced “Authentication Strength.” An ideal place to begin could involve removing phone and SMS authentication for privileged admin users or for accessing certain sensitive applications.
Maybe do a check first?
To see which users are using the voice or sms as an authentication method I created a powershell script. It displays the total amount of users and a list of which users are using sms or voice authentication.
# Install AzureAD module if not already installed
if (-not (Get-Module -Name AzureAD -ListAvailable)) {
Install-Module -Name AzureAD -Force
}
# Connect to Azure AD
Connect-AzureAD
# Get users with voice or SMS authentication
$authUsers = Get-AzureADUser -All $true -Filter "accountEnabled eq true" | Where-Object {
$_.OtherMails -like "*Voice*" -or $_.OtherMails -like "*SMS*"
}
# Display the count of users
$authUserCount = $authUsers.Count
Write-Host "Number of users using Voice or SMS authentication method: $authUserCount"
# Display the list of users
Write-Host "Users:"
$authUsers | Format-Table DisplayName, OtherMails
After this check, you can decide how to migrate users to a safe and secure authentication method.
Okey what do we need to do now?
There are some default authentication strengths defined in Azure:
- MFA strength – the same set of combinations that could be used to satisfy the Require multifactor authentication setting.
- Passwordless MFA strength – includes authentication methods that satisfy MFA but don’t require a password.
- Phishing-resistant MFA strength – includes methods that require an interaction between the authentication method and the sign-in surface.
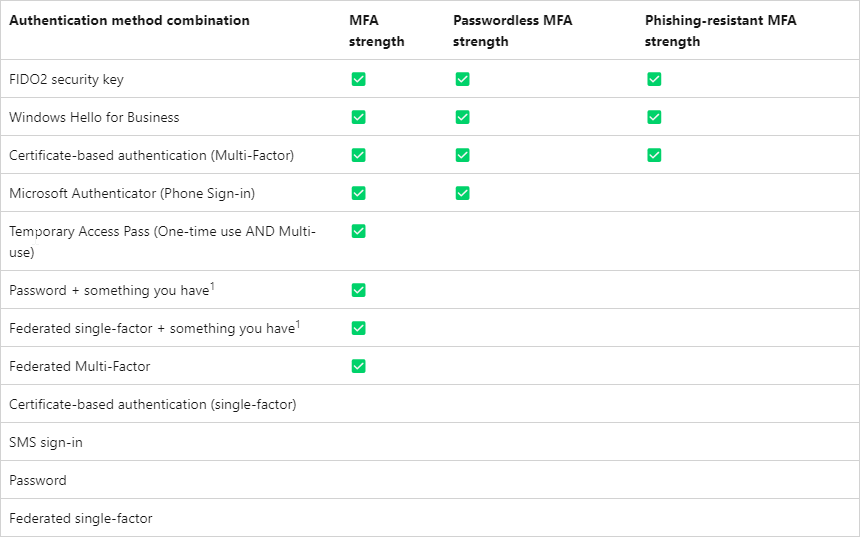
For now, we want to create a custom one because we only want to exclude voice and SMS from our authentication methods.
!!WARNING!!: If you configure Authentication Strength, be sure that you only trigger this for the right people and with the right settings. I had MFA already configured for my admin account, but this wasn’t working anymore, and configuring another method was not possible. I was really relieved that I had created an emergency admin account so I could access the Azure portal again and change these settings!
For now, we want to create a custom one without the possibility to use voice or SMS. When you go to the Microsoft Azure Admin Center, navigate to “Protect & Secure” and select “Authentication Methods.” On the right side, choose “Authentication Strength.” Here, you can select “New authentication strength.” I have selected the options as shown below.
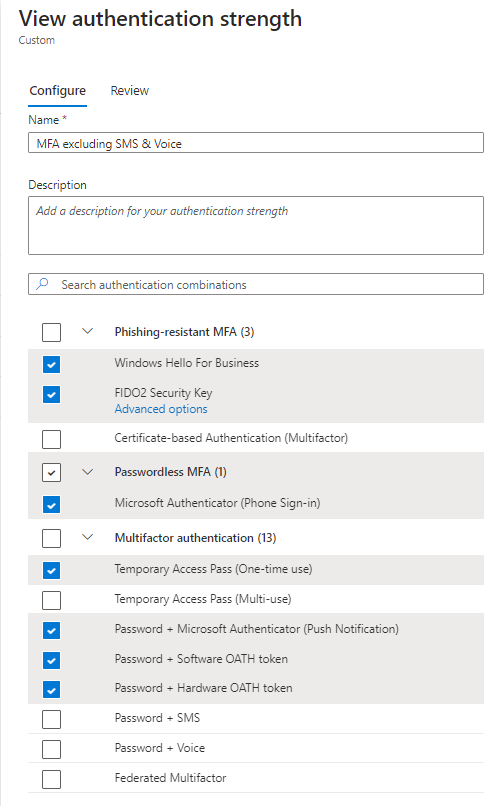
After this is created, I need to wait 10 minutes before I can change my conditional access policy. When you go to the conditional access policy you created for this group of users, you can select the “MFA excluding SMS & Voice” authentication strength.
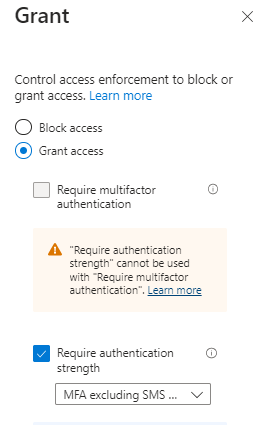
So, when all of this is created and saved, users with a weaker MFA will be prompted to step up to a stronger authentication method after attempting to log in.
Summary
In conclusion, multi-factor authentication (MFA) plays a crucial role in securing our digital world. However, not all MFA methods are created equal. While some are robust and reliable, others fall short in providing adequate protection against cyber threats. It’s essential to choose authentication methods wisely and migrate away from vulnerable options like voice and SMS authentication.
To assess the current state of authentication methods, a PowerShell script can be used to identify users utilizing voice or SMS authentication. By leveraging the power of Azure AD, the script provides valuable insights into the number of users and their specific authentication methods. Armed with this information, organizations can plan and implement a secure transition to stronger authentication options.
Microsoft’s introduction of “Authentication Strength” offers a promising solution. Custom authentication strengths can be created, excluding voice and SMS authentication, providing an extra layer of security. However, caution must be exercised when configuring authentication strengths to ensure the right settings are applied to the appropriate users.
By prioritizing robust authentication methods and gradually migrating users to safer options, organizations can fortify their security posture and safeguard against cyber threats. Multi-factor authentication serves as a vital defense mechanism, protecting sensitive data and ensuring the integrity of user accounts. With careful planning and implementation, organizations can navigate the complexities of MFA and build a resilient authentication framework.


Did you look at this one?
https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-system-preferred-multifactor-authentication
Setting the priority so that Fido will be the first authentication request.
Remco,
Thanks for your comment. That’s a good one.
I will take a look at it.